How to Identify Spear Phishing Emails to Protect Your Business
Recently one of our hosting clients noticed an email in his Spam box that appeared to have come from cPanel about his website hosting account. Although Gmail did the right thing by marking it as spam, the client wanted to make sure and emailed us to verify that this was spam and nothing more. This is an example of spear phishing scam, which Symantec defines as “an email that appears to be from an individual or business that you know. But it isn’t. It’s from the same criminal hackers who want your credit card and bank account numbers, passwords, and the financial information on your PC.”
If you think you will not be a target of a spear phishing scam as a small business, you might want to reconsider. In 2013, targeted spear phishing attacks against small businesses (1-250) accounted for 30%, according to Symantec. That’s 1 in 5 small businesses that were targeted in 2013. As a small business, not only are you a good target but you might be more vulnerable than a large enterprise due to lack of IT resources dedicated to security.
In this post, I wanted to outline a few tips to keep in mind when you receive a suspicious email that was sent from a vendor you’re working with – at least, it appears that way on the surface.
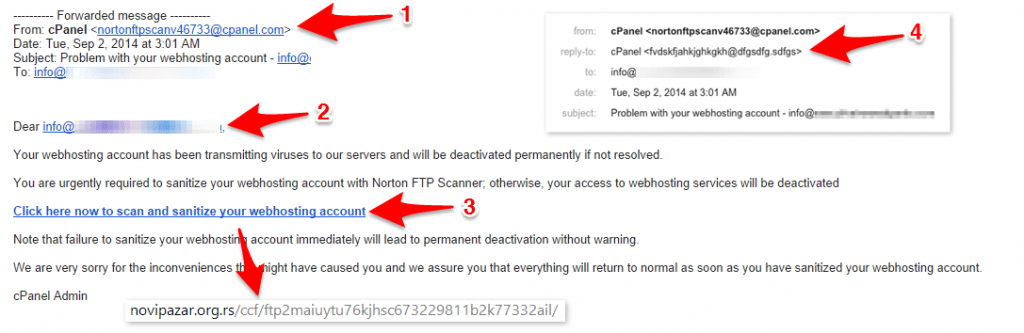
Let’s break down the spear phishing email using a real example that the client forwarded to us. Please refer to the screenshot with annotations above.
1. “From” Email Address
The FROM email address in phishing emails usually looks legitimate as if it’s coming from the actual vendor. That’s why it can be hard to spot a phishing email easily. When you know what you’re doing, FROM address can be spoofed to look like anything you want. If you’re suspicious of an email, don’t use FROM address to check its authenticity.
2. Dear Stranger
In many cases, scammers will only have your email address and not your name. If the email is addressed to something other than your name, in this example they used an actual email address, that’s another hint that it may be a fake email trying to steal your personal information. Granted, some businesses don’t use any greetings or might use “Friend” or similar greeting, but it’s not just one element that we’re looking at. It’s a combination of these elements in the phishing email that will help us determine if it’s fake or not.
3. The Link of Doom
Spear phishing emails cannot steal your information if you simply open them. In order to steal your private information they always ask you to do something – verify account, re-activate suspended account, etc. In our case, they were asking to scan and sanitize account for viruses.
Simply looking at the link text won’t tell you anything, but if you look at the URL where it takes you that’s a clear clue that this is a phishing email – completely fake!
In this case, it’s pretty clear that they are taking you to some weird website with a weird URL. In more elaborate scams, they will sometimes buy domains that are related to your vendor’s domain. For example, I recall an email from “PayPal” I received years back with the domain in the link being something like “PayPall”. It was a very small misspelling, which most people would never notice. And when you visit the phishing page, it looked exactly like PayPal’s page. Scammers go to great lengths to make spear phishing emails and pages as real as possible to increase their chances of getting information.
Few months ago, Symantec reported about Google Drive scam that had a login page that looked exactly like Google Drive’s login page, but was designed to steal your information.
We continue to advise users to enable Google’s two-factor authentication and to use up-to-date security software on endpoints and gateways.
If you have the slightest doubt that the email is a phishing email, ALWAYS play it safe and go directly to the vendor’s website or email directly to their support email you already know and use to verify email and any possible issues.
For our clients, you can either email directly to support@projectarmy.net (from a registered email address) or login to My ProjectArmy portal and initiate support ticket there. Also, you can email your Business Guardian directly to check on the status of your account or any other issues.
4. “Reply-to” Email Address
The last thing I wanted to mention was the “reply-to” email address. Even if “from” email address is spoofed to look like a legitimate email from your vendor, replying to that email will most likely either bounce or go to your vendor. But that’s not what scammers want, so they will insert some weird “reply-to” email address. So when you reply, they will get an email.
Check email headers to see what “reply-to” email is, and if it’s something you don’t recognize consider email to not be legitimate and contact vendor directly as I mentioned above.
For ProjectArmy clients, our notification and support emails will always come from either support@projectarmy.net or care@projectarmy.net to your registered email address. When you reply to them, make sure you’re replying to one of those emails unless you’re talking to your Business Guardian and have their personal work email.
If you have any questions about spear phishing emails, don’t hesitate to leave a comment and I’ll be sure to reply. And if you’re one of our amazing clients, you always have our team at your disposal. Don’t hesitate to get help. We’re always just an email away.
